webGuard
Introduction
webGuard is a Web Application Testing tool that helps find security vulnerabilities in your applications. webGuard uses OWASP ZAP as the backend and provides an easy to use intuitive User Interface to test an application. webGuard also has a robust REST API that can be used to hook up into build automation tools like Jenkins.
Architecture
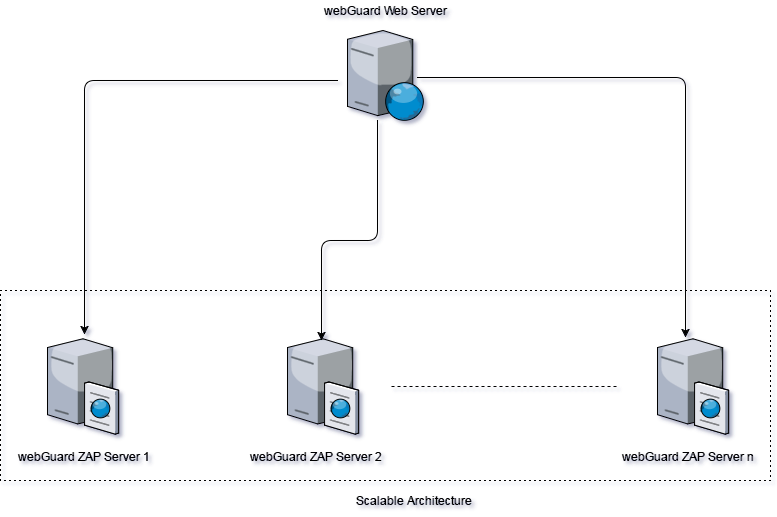
webGuard works on separate Web and ZAP layer. This ensures a scalable architecture to cater to increasing load. Multiple ZAP Servers can be spawned that work behind a single Web Server seamlessly and are managed to distribute load across these servers. Please refer to the image below for an overview of the architecture.
Installation
webGuard can be installed using the automated installer located in the GitHub repository here. To install the components, please follow the instructions below:
-
Clone this git repository:
git clone https://github.com/makemytrip/webGuard.git -
Run the install script by using the following command:
./install.sh -
On the installer screen, select the desired component to be installed, either Web Server or ZAP Server.
-
Depending on the type of installation, you might be prompted to enter more information. For e.g., when installing the ZAP Server you will be prompted to enter the Web Server IP for registering the ZAP Server. Please Note: It is required to have the Web Server installed and running before installing a ZAP Server.
-
Once installation is complete, point your browser to http://X.X.X.X (where X.X.X.X is the server IP where the Web Server was installed) to access webGuard GUI and http://X.X.X.X/admin for admin panel for Local user management.
Configuration
Login Method
webGuard supports 2 methods for authentication.
- Local DB
- LDAP
By default, the Local DB method is activated and uses the local MySQL database installed during setup to authenticate users. When this method is activated, webGuard serves as a self registration portal, where the user can register a username and password to login. There's no configuration for this method, except for a single variable in server/settings.py file:
# Login Method and Configuration
LOGIN_METHOD = "LOCAL"
When using LDAP Login, there is no registration option, as webGuard expects users list to be populated in the AD of the organization. If LDAP mode is selected, following variables need to be populated to properly authenticate in AD in the server/settings.py file:
# Login Method and Configuration
LOGIN_METHOD = "LDAP"
LOGIN_LDAP_SERVER = "10.0.0.2"
LOGIN_LDAP_PORT = 389
LOGIN_LDAP_DOMAIN_NAME = "domain"
Email Settings
webGuard can mail vulnerability reports to user email IDs. For a mail to be successfully sent, following variables need to be populated in server/settings.py:
# Email Server Settings
EMAIL_HOST = "mailserver.domain.com"
EMAIL_PORT = 25
EMAIL_FROM_EMAIL = "webguard@domain.com"
ZAP Server Settings
webGuard manages ZAP Instances running on servers by managing their memory utilization. By defining thresholds, webGuard will ensure that memory doesn't run out on servers and instances cannot be launched by users more than the specified limit. Following variables can be configured as desired:
# ZAP Memory and Instance count settings
ZAP_SERVER_MIN_FREE_MEMORY_THRESHOLD = 512 # Minimum memory that needs to be free on ZAP Server to start a ZAP Instance (in MegaBytes)
ZAP_MULTIPLE_ALLOWED = True # Allow or Disable running multiple ZAP Instances per user
ZAP_MULTIPLE_MAX_COUNT = 5 # if the above variable is set to True, how many maximum instances can be runper user
Usage
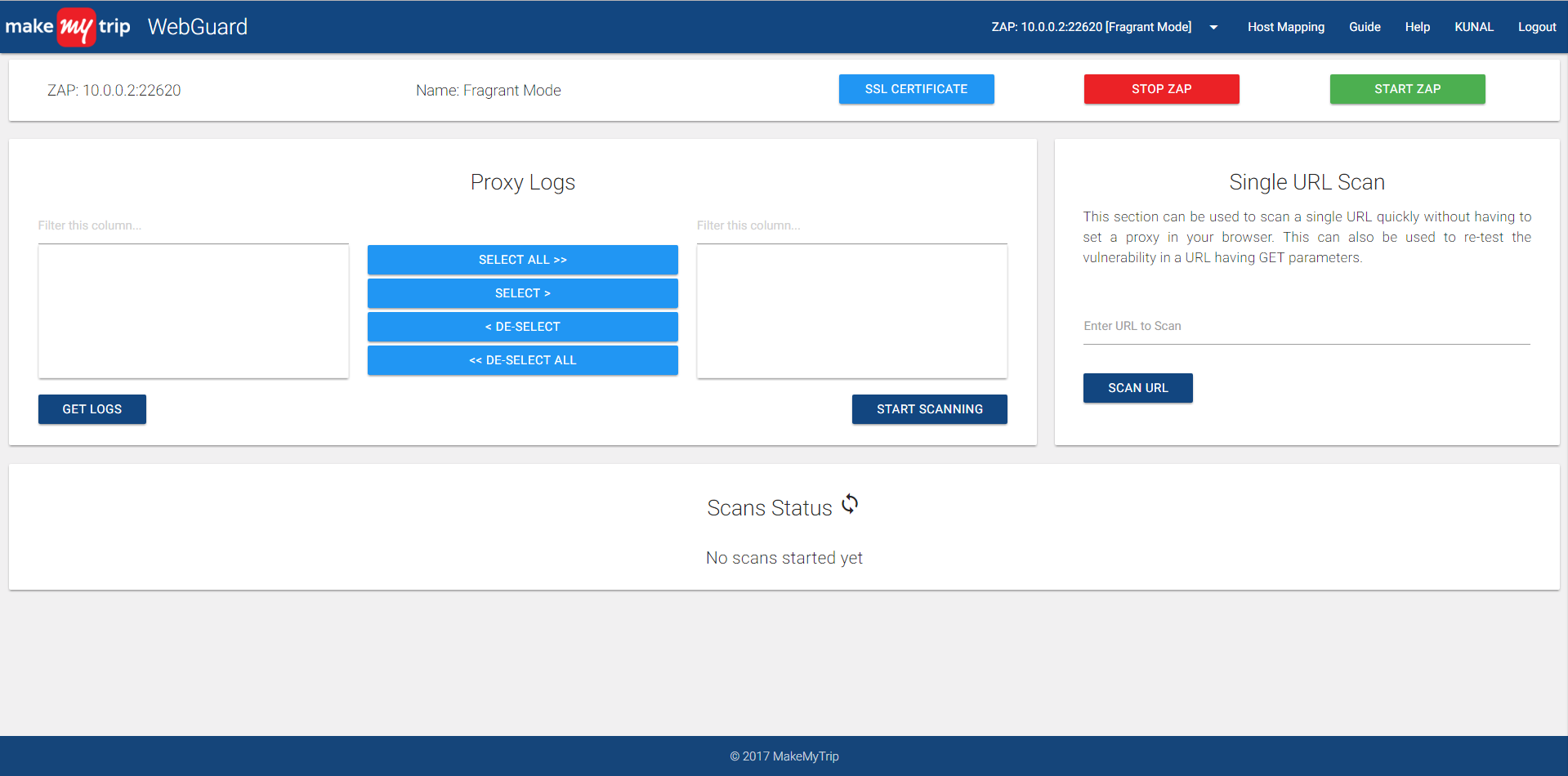
This is what a user's dashboard looks like after login.
For a detailed walkthrough of the application please refer the following youtube video.
API Documentation
webGuard is built up on a robust REST API that can be utilized for integration into automated build systems like Jenkins. The documentation for this API is available here.
License
This program is free software: you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. http://www.gnu.org/licenses/.